Week 1
Buffer Overflows
Who, me?

andrew.j.wong@unsw.edu.au
- Teams ^
- SECedu Slack -
featherbear
New number, who dis?
Share something interesting on your phone’s photo gallery (or meme collection) that describes yourself
Any society plugs hint hint
Housekeeping
🍉 Food - Sure thing
🎥 Recordings - Yes, next slide
👩🏫 Lab Attendance - Not marked
💡 This room has RGB lighting
Resources
Course Stuff
W11A
The W in W11A stands for WTuesday, duh
Don’t @ me it’s not my fault
Contact
cs6447@cse.unsw.edu.au
Slack - seceduau.slack.com
#cs6447#cs6447-21t2-w11a
Assessments
- Weekly Wargames (30%)
- Fuzzer Assignment (20%)
- Mid-term Exam (10%)
- Final Examination (40%)
Check the course outline for the schedule
RE: Wargames
They can be hard.. Start early!
“Most students should be able to do 75-80% of the challenges” - Adam 🍌
correct flag != full mark
Feel free to work together, but submit your own flags and tooling - more on this later..
Good Faith Policy
“These courses expects a high standard of professionalism from its students with regard to how security testing is conducted. We expect all students to act in good faith at all times […]”
TL;DR Don’t be mean
Kahoot
Kahoot now has a limit of 10 players on the free plan :(
Should write my own eh.
Lecture Review
Questions?
- Endianness
- ASLR
- Register layout (next slide)
- Buffer Overflows
- Stack Canaries
x86 Registers
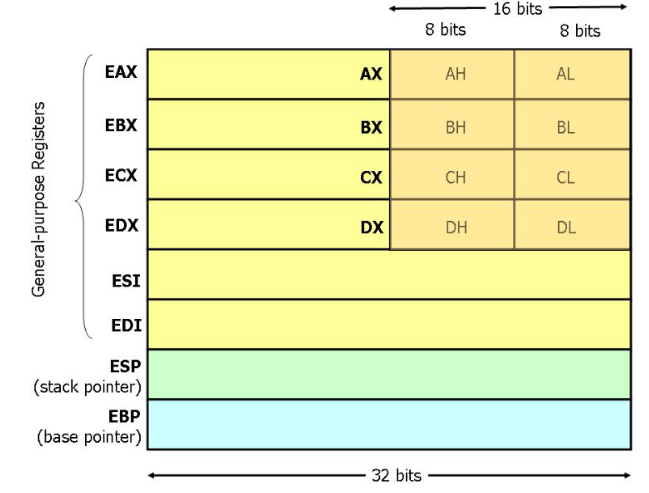
ebp, esp
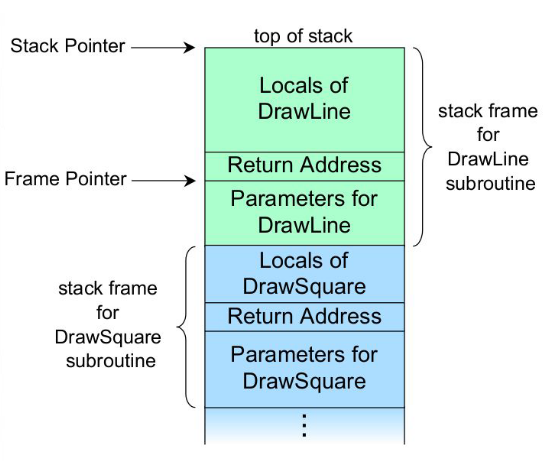
Buffer Overflows
[ | | | | | | | | | | | | | | | | | | | | | | | | | | ]blah
gets(data)
$> abcdefg...xyz
[a|b|c|d|e|f|g|h|i|j|k|l|m|n|o|p|q|r|s|t|u|v|w|x|y|z|-]blah
[ | | | | | | | | | | | | | | | | | | | | | | | | | | ]blah
gets(data)
$> abcdefg...xyzAAAAAAA
[a|b|c|d|e|f|g|h|i|j|k|l|m|n|o|p|q|r|s|t|u|v|w|x|y|z|A]AAAAAA
Your Hacker Environment
- Linux (or WSL - maybe)
- Binary Ninja
- pwndbg
- pwntools
pwndocker
Demo
Your Turn
[WebCMS] > [Labs] > [Lab 1]
- One binary, two vulnerabilities
- Don’t look at the source code, unless you’re really stuck!