Week 4
Good Faith Policy
“These courses expects a high standard of professionalism from its students with regard to how security testing is conducted. We expect all students to act in good faith at all times […]”
TL;DR Don’t be mean
SUHHHHHHH
LOOOOOOOO
SHOOOONZZ
Challenge walkthroughs, cool things?
Topic 2 Review
User Identity and Authentication
Weeks 2 - 3
- Authentication
- Validating the user is the identity they claim
- Authorisation
- Giving the user access based on their identity
Don’t do this.
Information disclosure baaaad.
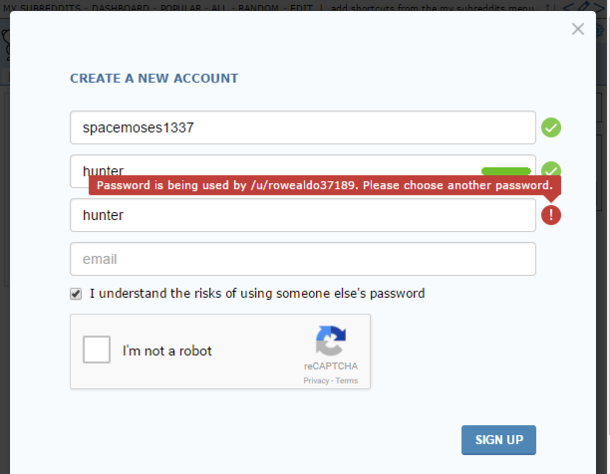
Hashing
- Hashing is not encryption
- One way function
Salts 🧂
Random bytes that are mixed into a passphrase to modify the hash values.
- Increases entropy
- 🌈 Mitigates rainbow table attacks
Recon
- Active & Passive Recon
- DNS Recon
- Directory Enumeration
- Protocol Headers
Preventing Spam
- Captcha
- Account Lockout
- Rate Limiting
C is for ______
Don’t use cookies to store important stuff.
If you have to, secure it.
- HTTP Only
- “Secure” mode
- Encrypt the cookie
SQL
- Structured Query Language
- MySQL, SQLite, PostgreSQL, Microsoft SQL, NoSQL
- Statements
SELECT _ FROM _ ...INSERT INTO _ (COLn, ...) VALUES (VALn, ...)UPDATE _ SET _ = _ ...DELETE FROM _ ...... -- this is a comment- …
- WHERE
>- greater than<- less than=- equal to<>- not equal to- …
- LIKE
%- wildcard
- UNION
- …
Demo:
stocktable
SELECT,INSERT,UPDATE,DELETE- Fingerprinting
@@Version- Microsoft SQLVersion()- MySQLsqlite_version()- SQLite
- Functions
- Schema / Meta
SQLi
user input = dangerous
'";<lol/>../--#`ls`
- What?
- User input contains control characters that interfere with the syntax of the SQL statement
- Why?
- Bad programming
- User input is ‘trusted’ to be valid and reasonable
How
SELECT a FROM b WHERE a = '$userInput'
Using ' OR '1'='1
vvvvvvvvvvvvv
SELECT a FROM b WHERE a = '' OR '1' = '1'
^^^^^^^^^^^^^
Demo: login 1, login 2
Step 0: Figure out the syntax, and fingerprint if needed
- Bypass logins
- Extract data
- Spoof a user -
USER_DOESNT_EXIST
Mitigating SQLi
- Disable debug logging
- No error messages, maybe just a blank screen?
- WAF - Web Application Firewalls
- Strip out malicious payloads™
- …or completely block access
- Parameterised Queries
Demo: login 3
Defeating mitigations
- Payload stripped? Embed dummies
- Blank response? Side channel attacks
- Timing Attacks
- Out of Band Attacks
- i.e inbuilt functions (therefore fingerprint!)
- Error-based extraction
- Boolean-based extraction
- Subqueries
SELECT a,b FROM c WHERE d UNION SELECT (SELECT ...), 2
Note
- Sometimes you need to big brain the payload
- i.e. yesterday’s lecture demo
- Reporting a vulnerability
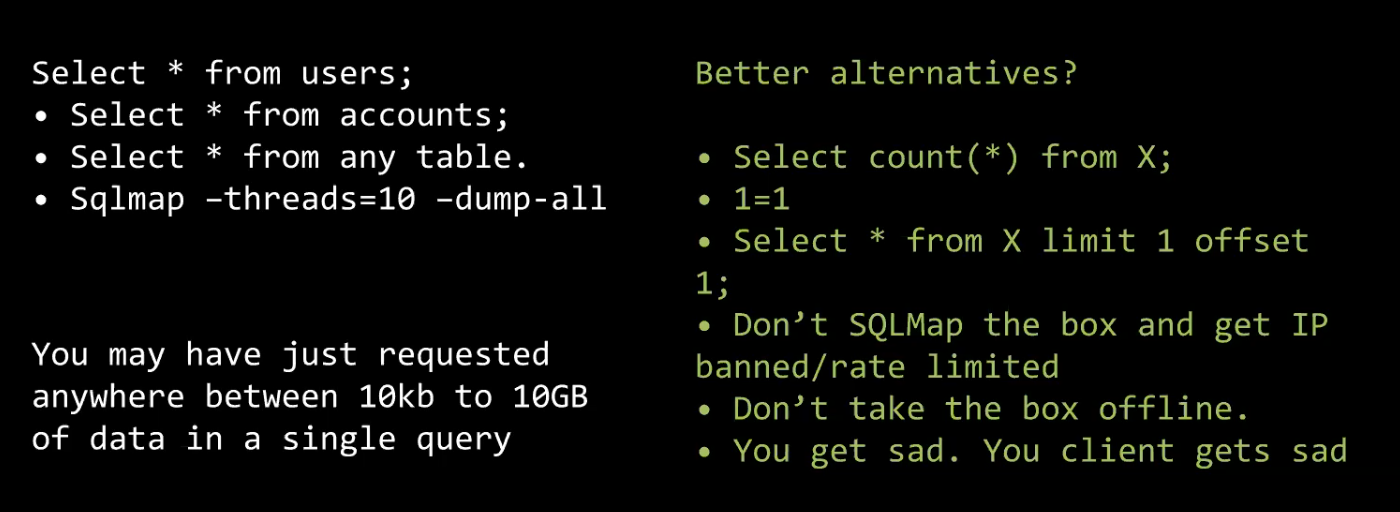
!=extracting data - SQLi payload list
- Big database? -
COUNT()it instead
Other Injections
MongoDB (NoSQL)
- JSON
- Data is transmitted as strings
- Escape the string?
Local File Inclusion
http://website.com/getImage.php?file=image.pnghttp://website.com/getImage.php?file=/etc/passwd
Server Side Template Injection
e.g. Jinja templating (Python + Flask)
{{ "hello " + "world" }} => "hello world"
{{ "".__class__.__mro__[1].__subclasses__() }}
^ the `object` class
You now have a handle to every function. welp.
Mid-sem Exam
- Week 5 - Tuesday 5pm - 6pm
- Lecture afterwards
- Locations: in-person / remotely
- Practice
Deliverables
- New topic, new challenges!
- This topic’s challenges due next Sunday 23:59pm
- Report - Week 7