Week 3
Good Faith Policy
“These courses expects a high standard of professionalism from its students with regard to how security testing is conducted. We expect all students to act in good faith at all times […]”
TL;DR Don’t be mean
About marks
- Apart from Topic 1 challenges (Recon), all challenges are awardable.
- Challenges in the criteria outline the credit mark
- Full marks = do all the challenges
SUHHHHHHH
LOOOOOOOO
SHOOOONZZ
Challenge walkthroughs, cool things?
HAAS, Recon, …
Bonus marks!!!
ALPACA

Application Layer Protocol (A…) Confusion (A…)

- Confusion Attack
- MITM capability allows access to other secured services that share SSL/TLS certificates.

- Lots of requirements for the vulnerability to work
- Mitigations
- SNI - Server Name Indication
- ALPN - Application-Layer Protocol Negotiation
- Unique SSL/TLS certificates - Let’s Encrypt
Upcoming
Mid-semester Exam - Week 5
- Locations: In-person, also available remotely
- Practice
Report 1 - Wednesday 11:59pm - Week 7
More recon
recon Social Engineering
(140).jpg)
Thanks for your birth date <3
CSP
Content Security Policy
Images, scripts, styles, etc can only be fetched from certain locations.
- i.e. Only HTTPS sites
- i.e. Only certain websites
More on this in later weeks…
MITM
Man In The Middle
Attack: HTTPS Downgrade
- HTTPS = more difficult to intercept
- HTTP = easily interceptable
MITM: “Actually, let’s use HTTP instead”
Defense: HSTS
HTTP Strict Transport Security
- A list of HTTPS-only sites
- HSTS Preload List
- Hardcoded into major web-browsers
Authentication vs Authorisation
authentication!= authorisation
Cookies Bad
Don’t use cookies to store important stuff.
What if we have to?
Cookie Protection
- HTTP Only - Not accessible through JS
- Secure - Only for HTTPS
base64 encodingno.
Access Control
- DAC - Discretionary
- ABAC - Attribute-Based (Meta)
- RBAC - Role-Based (Groups)
- MAC - Mandatory (Levels)
SSO and FID
SSO - Single Sign On
- Access to multiple services with the same session
- Note: Terms are often used incorrectly
Same credentials for multiple services
FID - Federated Identity
- External authentication validation
OAuth
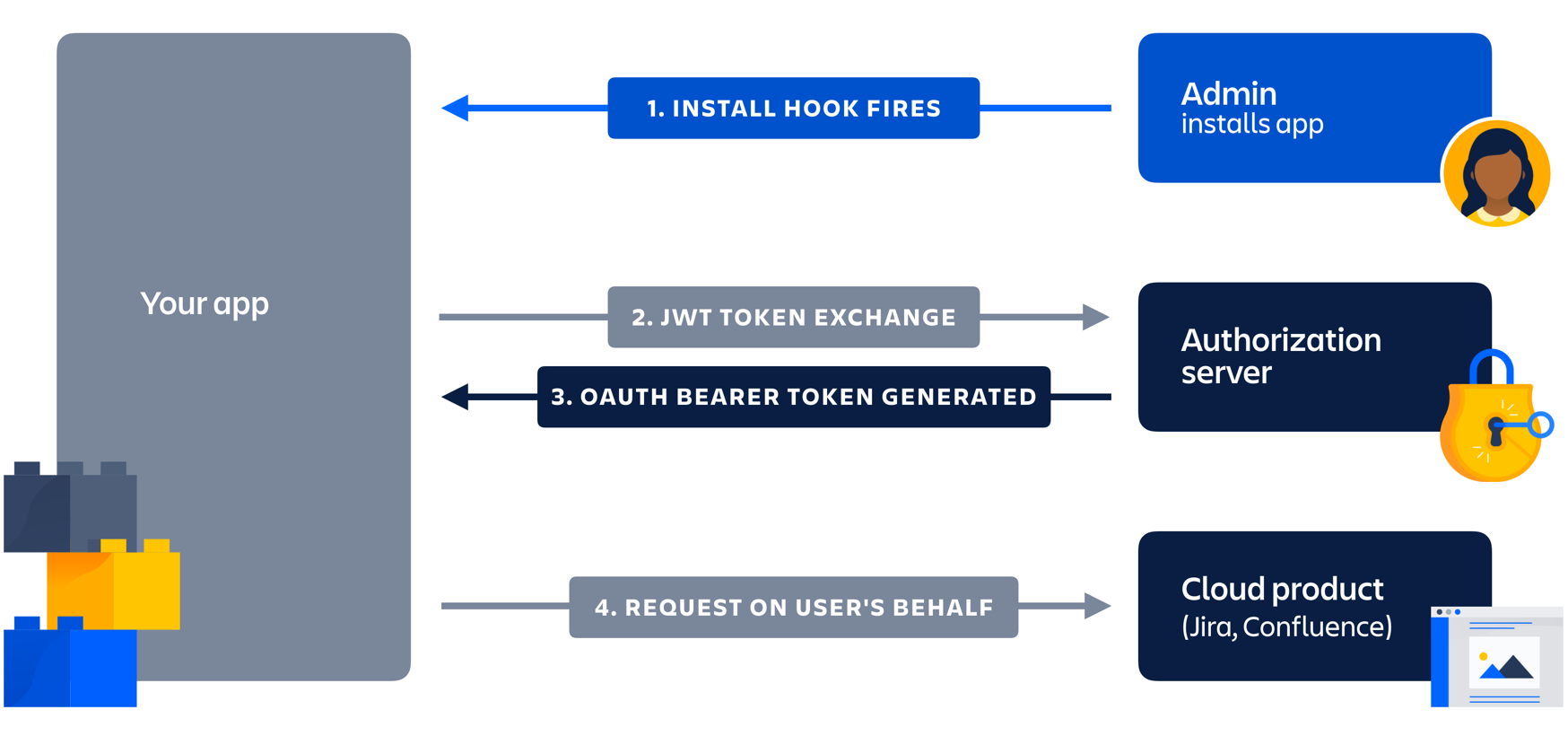
misc
Anything else you want me to rant about?
Note to self: scripting
Deliverables
- This topic’s challenges due THIS Sunday 23:59pm
- Report - Week 7