- Firmware is upgraded incrementally rather than straight to the latest version
- Probably because of dependencies, etc
Process
- Download to blk10
- Flash blk10 to blk9
- Boot into blk9 (new)
- Flash blk10 to blk8
Upgrade Log
The original firmware that was on the device was 01.15.58
There was an upgrade notice to go to v01.17.08
Once upgraded, there was another upgrade to go to 01.17.08
Once upgraded, there was another upgrade to go to 01.19.98
I think I got locked out at this point, because the UART shell didn’t accept my root credentials
Files That Are There?
- /usr/sbin/tcpdump
- Call to tcpdump in /opt/rockrobo/wlan/wlanmgr
- /usr/bin/scp
Notice
- Newer versions no longer use the
vindafile, and usean embedded linux OS rather than Ubuntu 14. Now usesbusybox.- Edit:
/etc/os-releasestill seems to suggestVERSION="14.04.3 LTS, Trusty Tahr", but the system is much more heavily locked down
- Edit:
- The serial/console login seems to be handled by
/sbin/rr_login- Tries to access
/mnt/default/shadow- but it doesn’t exist on the system and hence always errors out - We can modify
/etc/inittaband switch out/sbin/rr_loginfor the default login handler
- Tries to access
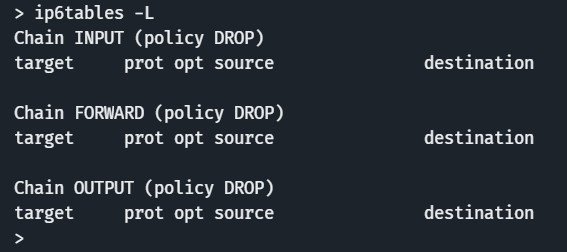
- IPv6 is blocked with
ip6tables - Dropbear is used as the SSH server
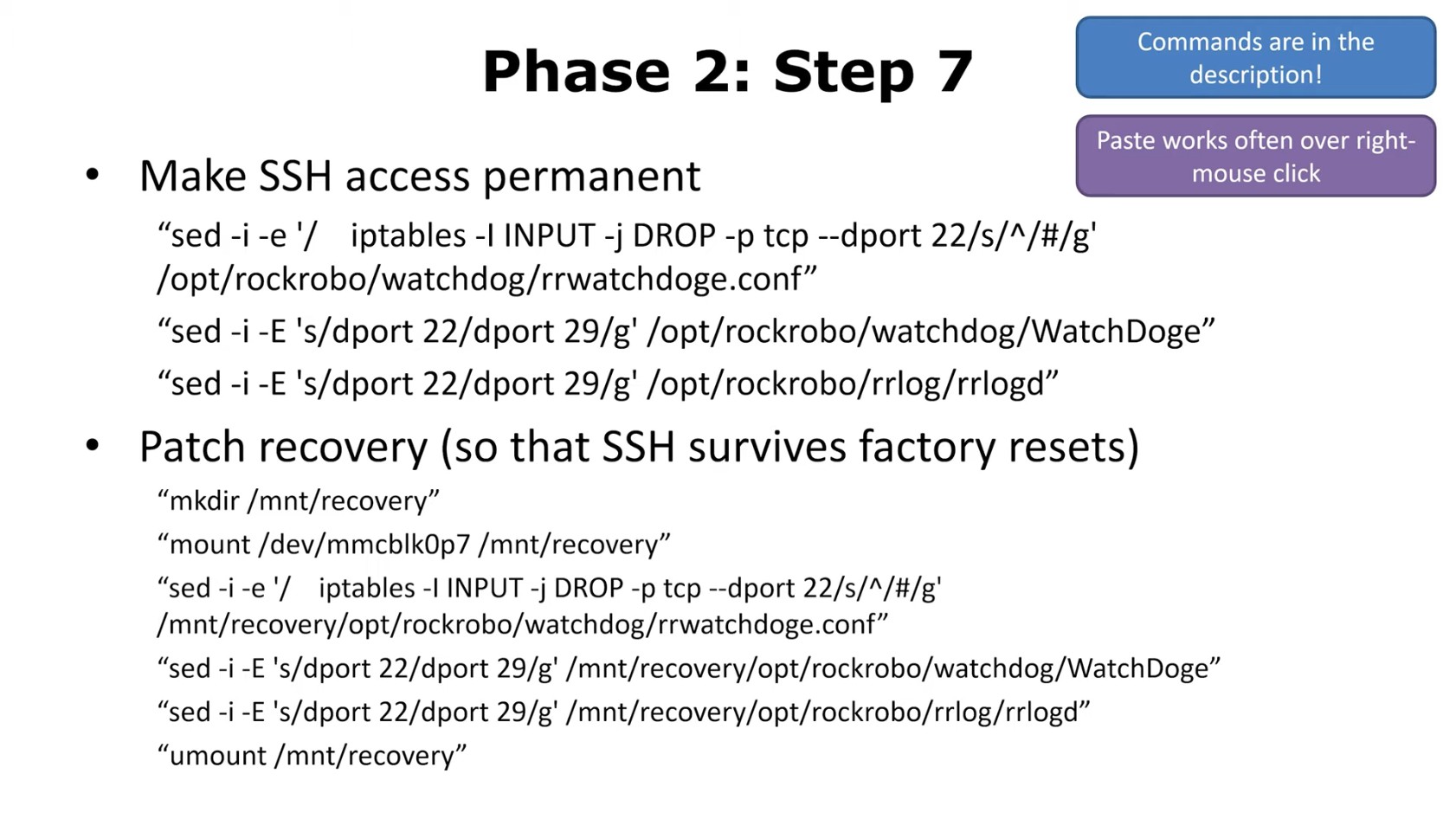
- The
WatchDogeprocess will re-run the iptables SSH drop rule, rendering simple conf commenting void - Have to patch
WatchDogeto null the iptables command
- The
- The
rrlogdprocess has been upgraded to drop SSH (iptables) if the system model version check enters the false branch- Also need to patch
rrlogdto null the iptables command
- Also need to patch
/opt/rockrobo/wlan/wlanmgrhas the ability to calltcpdumpduring debug mode
Supposedly Giese realised this in 2020 as well oop