2018 - Michael Steigerwald (VTRUST)
Talk: Smart home - Smart hack
- Products from different manufacturers used the same cloud infrastructure (with supposed ‘military-grade security’), each with their own ‘customised’ (white-label) smartphone apps
- Used the Espressif ESP8266 chip
- WiFi-enabled SoC with Arduino support
- Often used by tinkerers and enthusiasts
- Anyone can become an ‘IoT company’ regardless of “having in-depth technical knowledge of IoT or IT security.”
“The analysis of the ‘smart’ devices using this basic platform is generally frightening […] serious […] shortcomings”
- Insecure transmission of encryption keys, serial number, etc…
- Insecure transmission of wireless credentials during pairing
- Ease of white-labelling and starting your own IoT business
- Ease of selling malicious devices
Automated flashing tool tuya-convert created that exploited prior vulnerabilities to flash custom decoupled firmware
(i.e. ESPhome, Tasmota, etc…)
Tuya’s Response
- 28th January 2019 - patch released (later subverted)
- TLS encrypted firmware update procedure
- Encryption of flash memory
- 3rd January 2020 - new patch released
- unbreakable™
- 23rd April 2020 - Switched from the ESP8266 to a custom SoC
- 16th June 2021 - Announced official support for HomeAssistant
LIDARPhone - 2020 - Acoustic Eavesdropping
- LIDAR sensor detects minute vibrations that are induced on objects near audio sources
- Vibrations are extracted and turned back into sound waves
- Extraction of sensitive data (i.e. credit card digits)
- Achieved 91% classification accuracy
Flash Dumping
- Requires a flash programmer ($$$)
- Budget Solution: Raspberry Pi?
- Some flash chips (depending on form factor) may require to be desoldered
- Possibly a destructive process
- Free software:
flashrom
BGA shorting to gain access to FEL
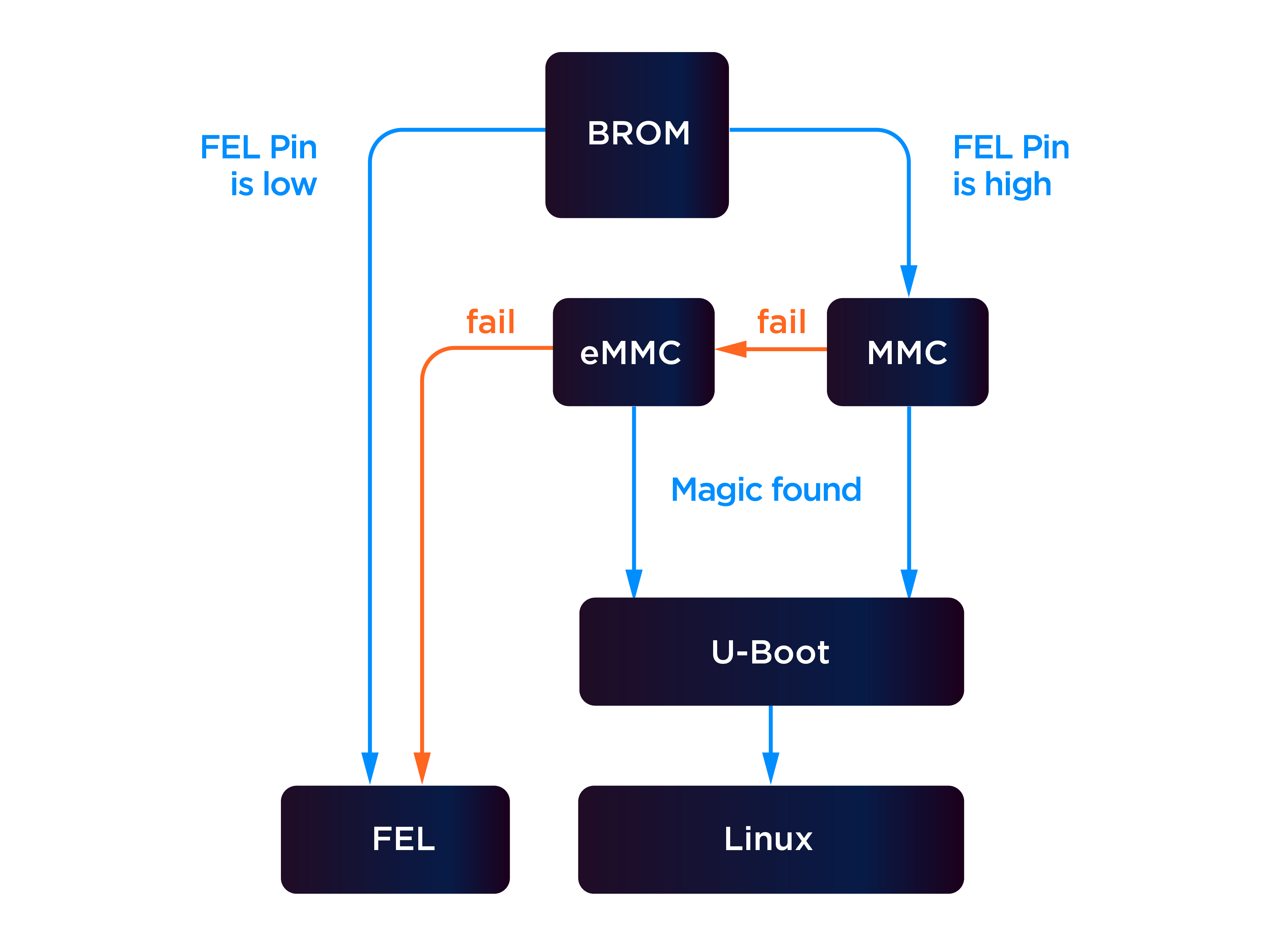
- FEL mode is a “fallback” system on Allwinner SoCs that allows flashing
- Generally triggered by pulling the FEL pin to LOW during boot
- On the Allwinner R16 (BGA), located on ball L14
- Ball not located on the edge of the chip and so required desoldering / breakout
- On the Allwinner R16 (BGA), located on ball L14
- FEL mode can also be entered if U-Boot (or another bootloader) fails to load 🤔
- The Allwinner R16 (used in the Roborock) has a solder plane height of around 0.3mm
- Too shallow for a wire
- Aluminium foil has a thickness of ~0.02mm
- Aluminium foil is conductive…
- $
- Enter FEL mode by corrupting the eMMC reading
Documented: SEEMOO-MSC-0142
Aside (2021)
Dennis discovered that on the Roborock S7, TPA17 (on the circuit board) connects to ball L14 on the SoC.
By pulling TPA17 / L14 / LRADC0 low (i.e connect to GND), FEL mode can be entered
Infrastructure Security
- Sensitive information inside logs
- Client-side access management
- Certificate pinning bypass-able
Vacuums in the Cloud: Analyzing Security in a Hardened IoT Ecosystem
https://www.usenix.org/conference/woot19/presentation/ullrich
- AM335x Microprocessor
- ARM Cortex-A8
- Cold-boot attack
- USB + Serial communication allowed boot into custom image
- RAM could be dumped to the serial port
- Extraction of keys
- Auth/Authz to the robot AND cloud
- Secret key RNG weak - able to bruteforce
- RSA key was shared with all devices
- Identity impersonation
- Logs and coredumps were encrypted :)
- But encryption keys were hardcoded :(
- Buffer Overflow -> RCE
2014 - Large-scale Firmware Analysis
- Broad analysis of a large number of firmware images
- Discovered 38 new vulnerabilities over 693 images
- Similarities in vulnerabilities
- Static analysis and extraction of keys, credentials, configs, other ‘tells’
Fuzzy Binary Analysis
https://github.com/ReFirmLabs/binwalk
https://github.com/ssdeep-project/ssdeep
https://github.com/sdhash/sdhash
- Source code changes largely remain the same
- But binary files change ‘arbitrarily’
- Difficult to compare binary files
- Calculate fuzzy hashes instead to compare similarity
IoT | 2017/2018 - Xiaomi Dafang Hacks
- Cheap WiFi camera that can be made to boot off a microSD card
- Circuit board exposed UART (
baud_rate=115200) pins that allowed interaction with U-Boot bootloader - Modification of boot environment to start
/bin/sh([link]) - Gain root shell access
- Dump firmware
- Analyse, modify and package updated firmware
Xiaomi Ecosystem | 2017-2019 - Dennis Giese
Paper:
SEEMOO-MSC-0142(July 10, 2019)
- Research available: dontvacuum.me
- Performed security analysis of a range of Xiaomi products
- Found ways to root the Mi Home Robotic Vacuum Cleaner and the Roborock S6
- UART, hardware fault injection, etc…
- Developed cloud emulation software (DustCloud)
- Research led to development of 3rd party software (i.e. Valeduto)
“How secure is the implementation of the ecosystem of the IoT market leader Xiaomi?”
Conclusions
- ⌚ The company quickly responds to security concerns
- 🔍 Many exposed endpoints of deprecated APIs
- 🔓 Many devices do not enforce proper HTTPS checks
- 🤝 Difficult to enforce security for plugins (vendor-provided)
- ❓ CIA principles generally kept