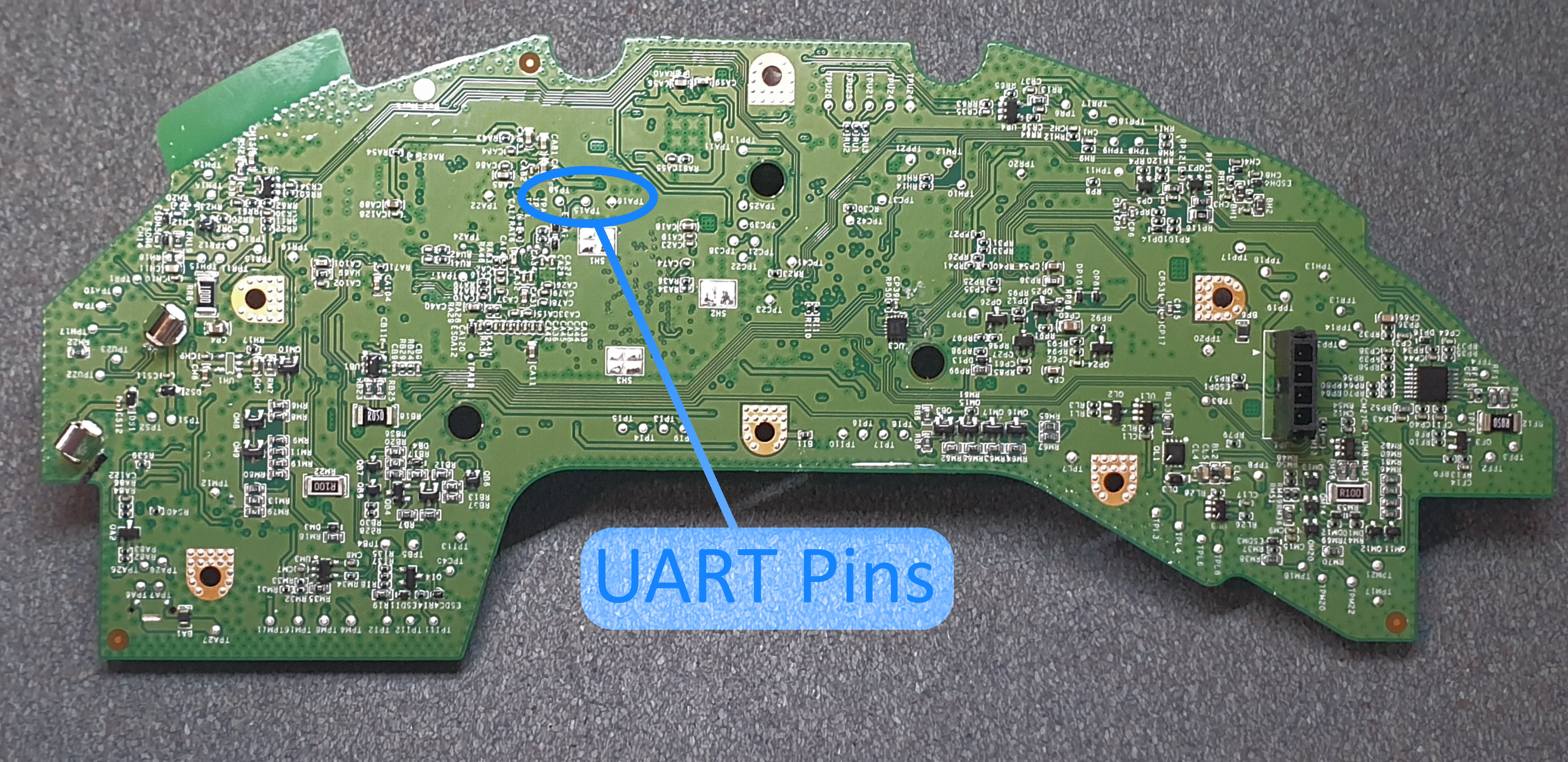
Removed the logic board from the robot and had a look at the pins near the Allwinner R16 processor / SoC. Read Dennis' writeup about the UART pins being located on RX:TPA15, TX:TPA8, GND:TPA16
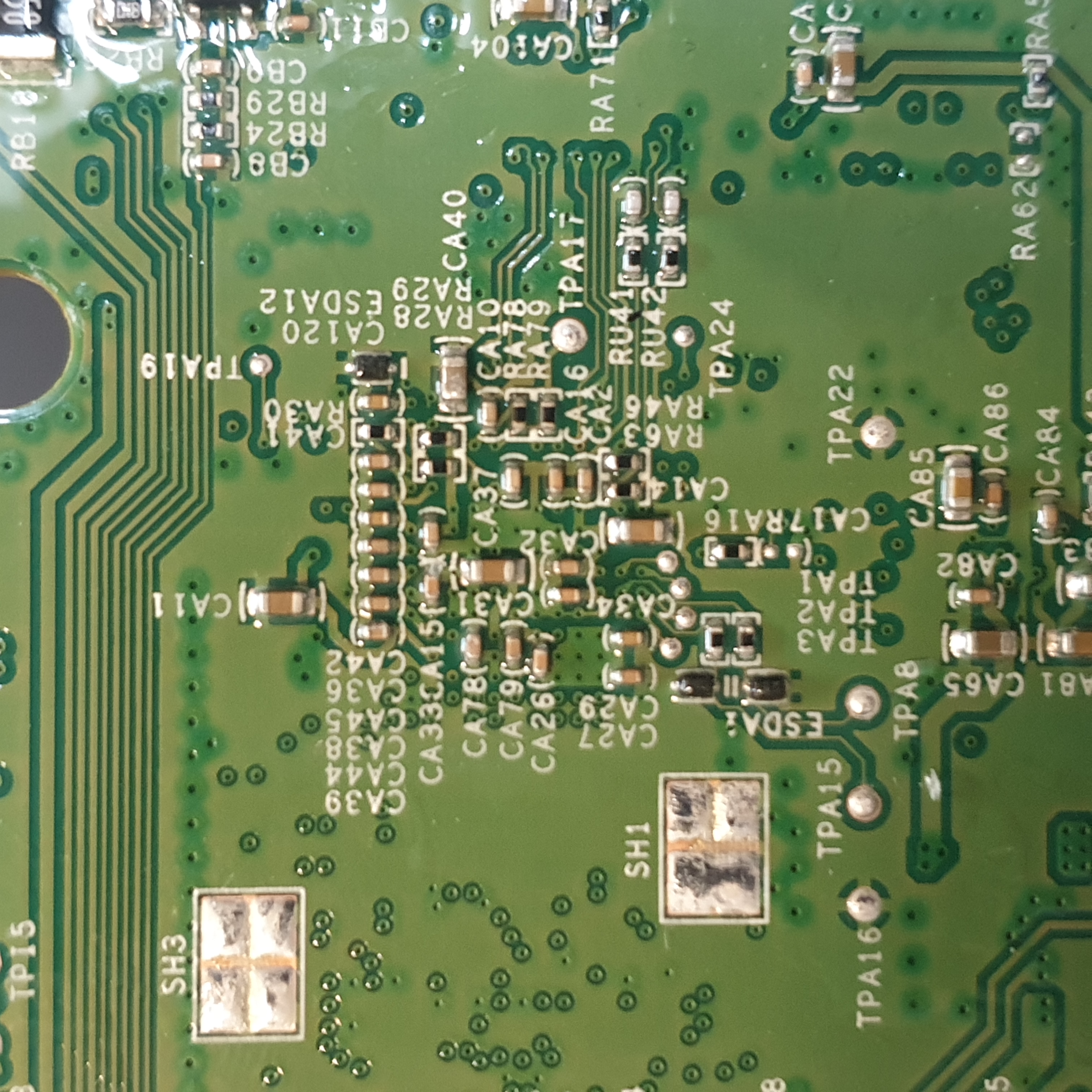
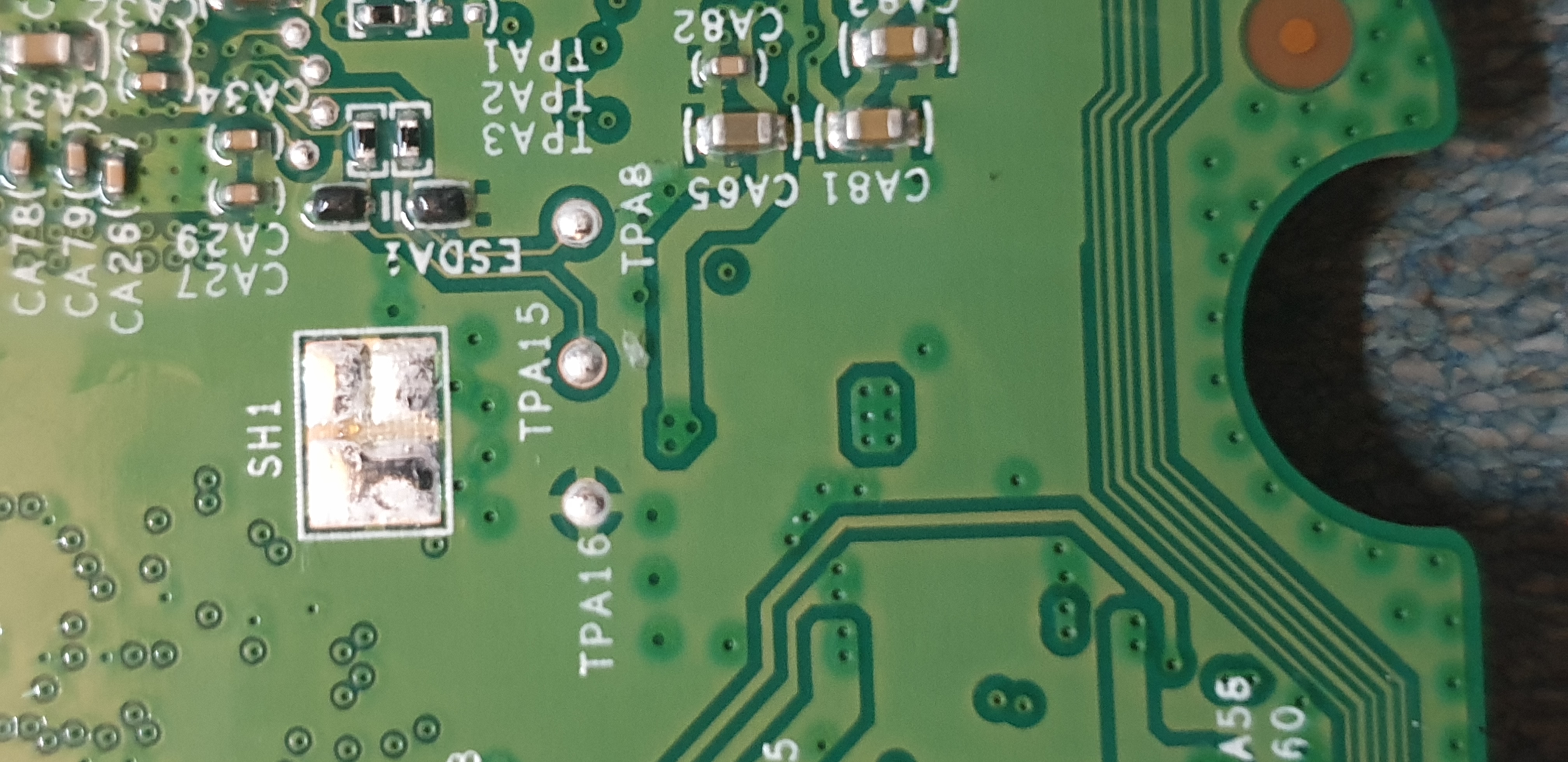
I then soldered some wires onto the test pins (too hard to just hold it with my hands)
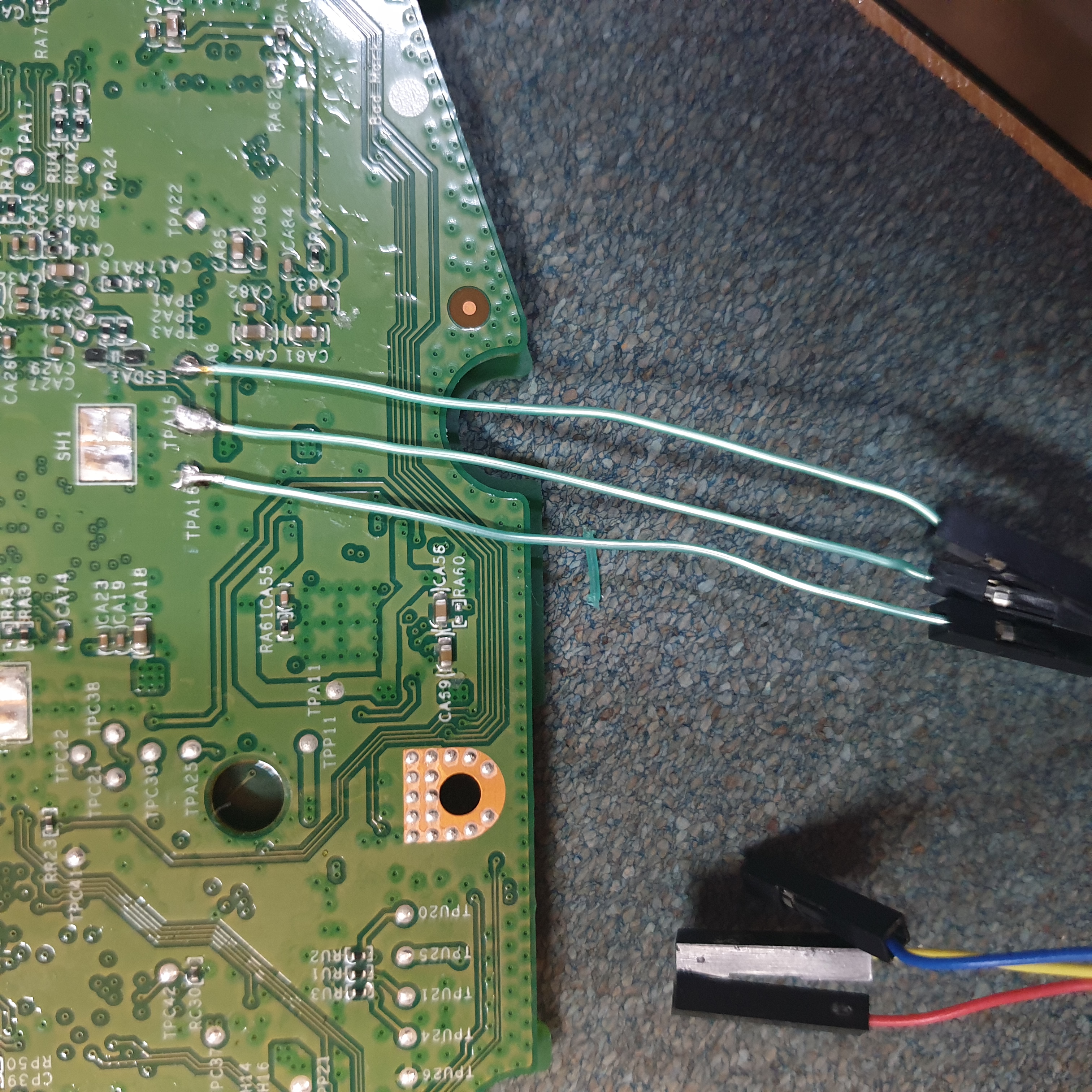
Was able to connect to the device with baud rate 115200.
Read [here] for the communications dump.
According to these lines in the uboot source code holding s drops us into a shell
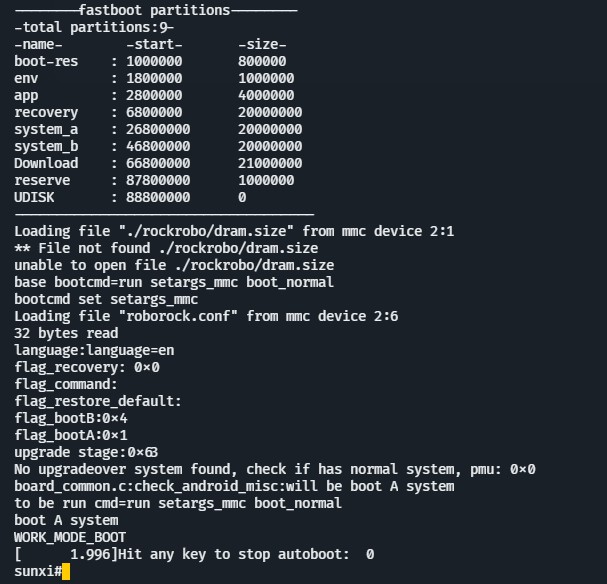
After enumerating through the different partitions, we can find the file vinda in emmc device 2, partition 6. This file contains an XOR(0x37)’d copy of the root password
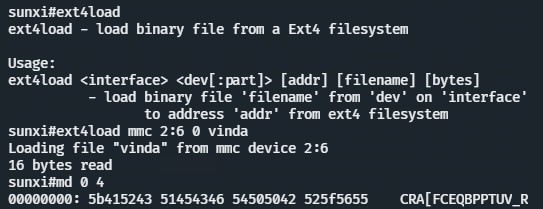
After the decryption, we’re root!
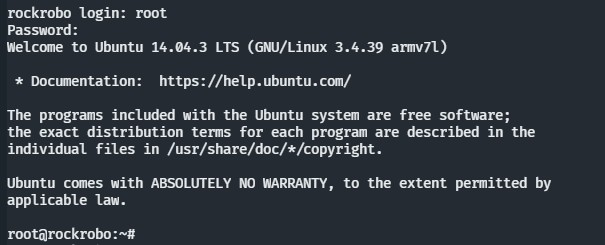
Also had a quick look at the best ways to back up the filesystem (for analysis).
Later will also need to see what online analysis things there are to do